OPSEC - Presentation Slides
OPSEC
Protecting your goshdarn privacy in the
Age of frickin Data Mining
**docs.chrisparsell.com**
OPSEC [ˈäp-ˌsek] noun
Short for Operations Security.
A process used to protect sensitive information from being accessed, exploited, or misused by adversaries.
It involves:
• Identifying critical information
• Analyzing potential threats
• Implementing protective measures
via The Economist (2017)

via WebFX
Your frickin data trail
Alex searches for "running shoes for flat feet"
Alex's smartphone
Alex is IRL
Types of data you hand over:
- Personal identifiers (name, address, age, etc.)
- Behavioral data (clicks, views)
- Location and motion data
- Health info
- Psychographics
I. How your darn data are collected
Everyday actions:
- Web browsing & trackers
- Phone sensors & GPS
- Smart devices & wearables, vehicle data
- Offline sources (Loyalty programs & purchases)
Real examples
image via SendPulse
Personalized recommendations
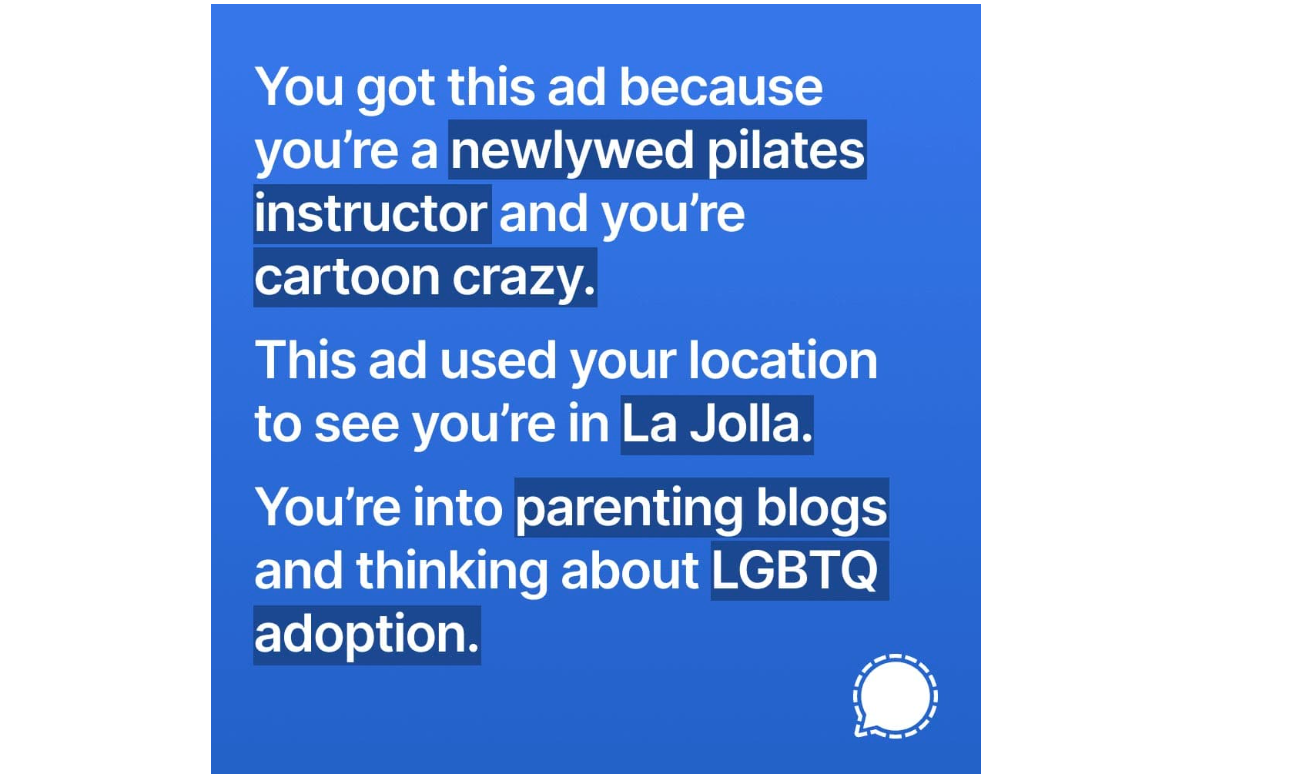
via CPO Magazine
Targeted Advertising and goshdarn Marketing
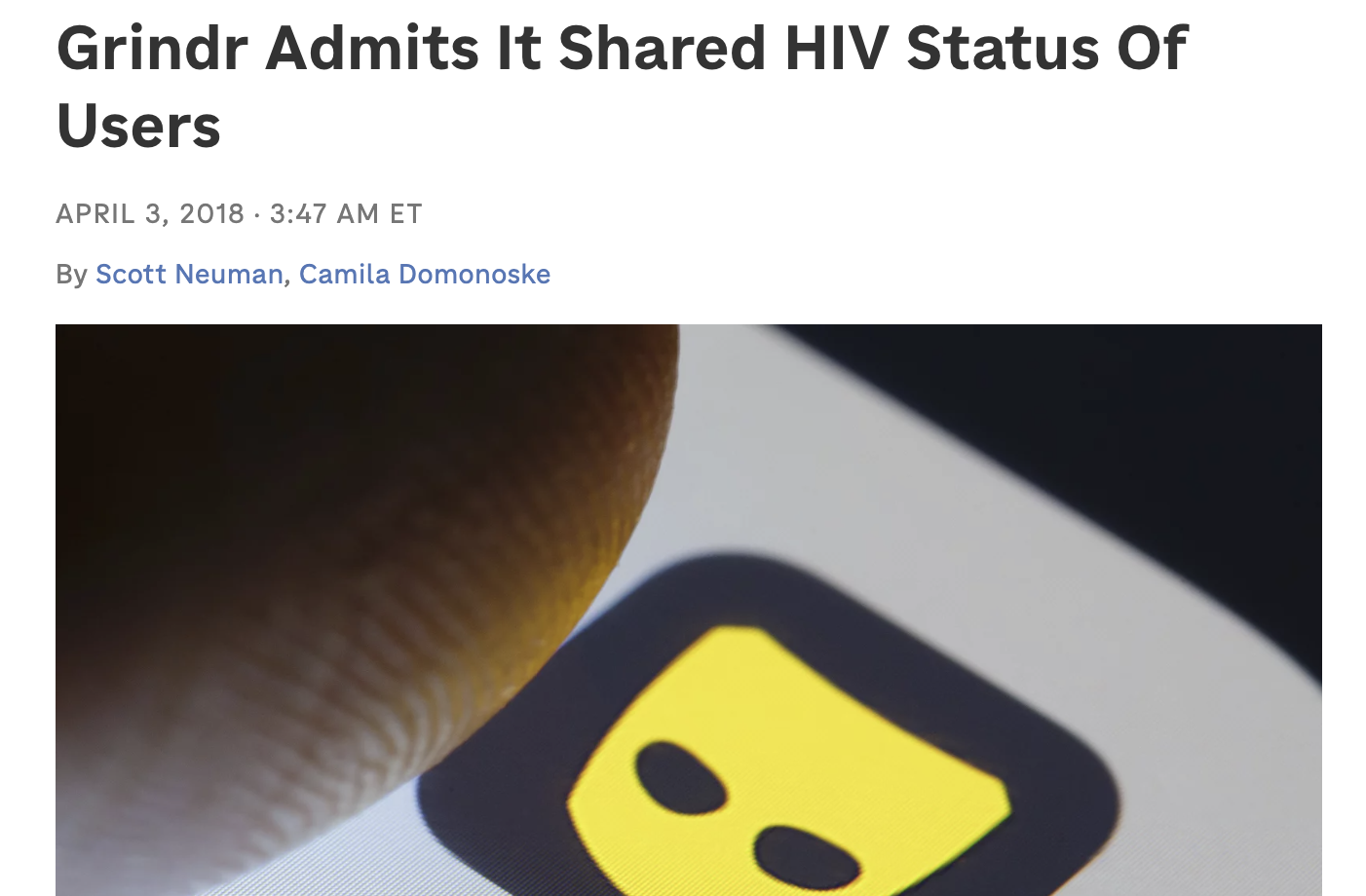
via NPR
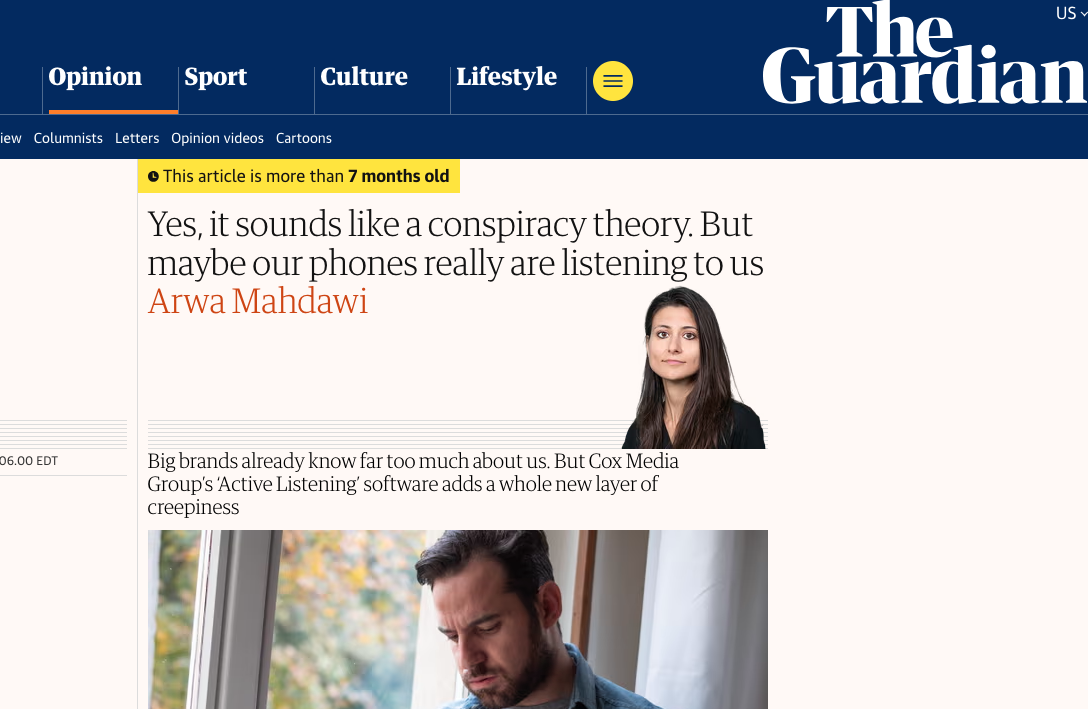
via The Guardian
Is your phone listening?
Insurance Risk Scoring and Profiling

loan and credit evaluation
via PSI
Employment screening
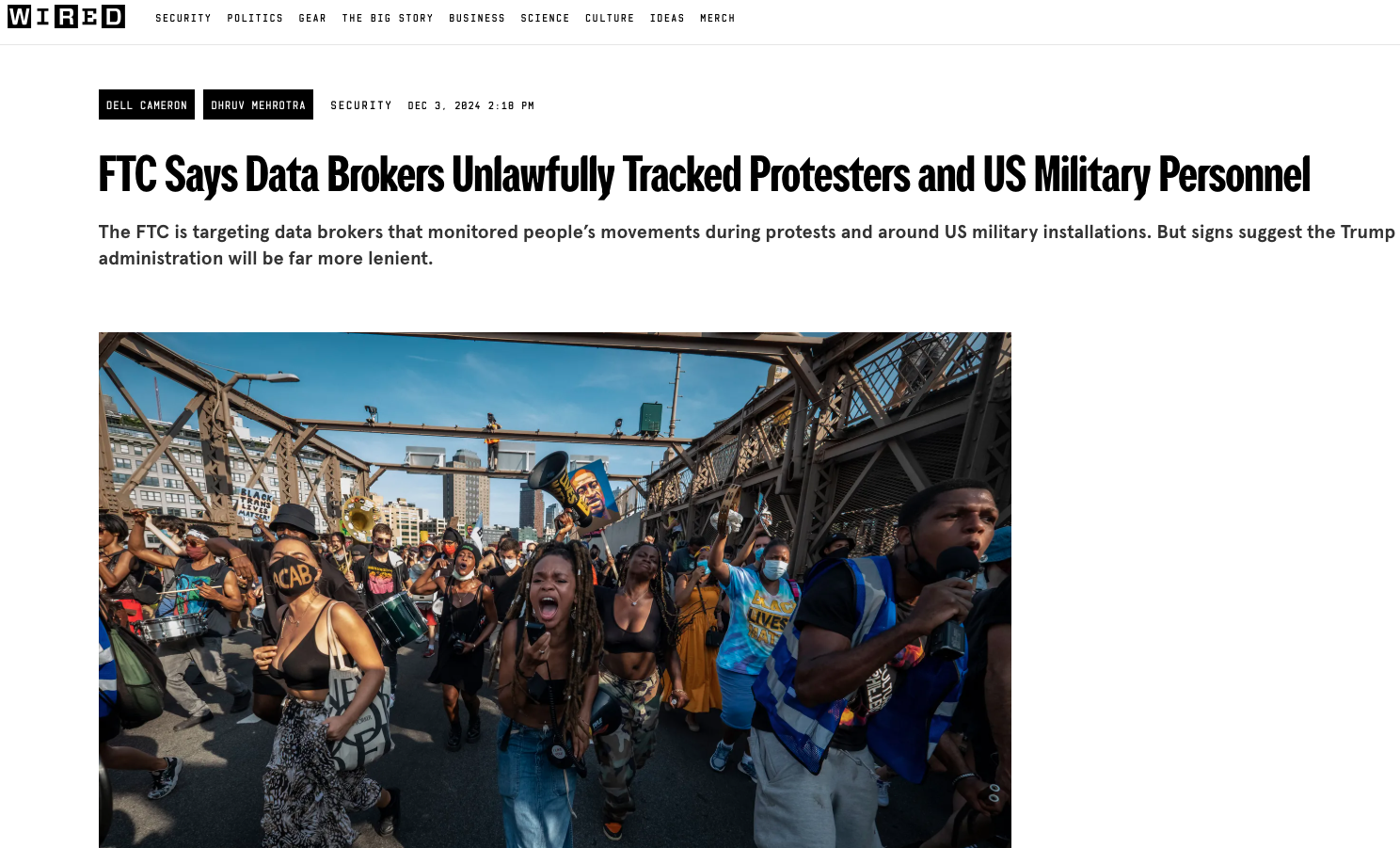
via WIRED
Surveillance and lovely Law Enforcement
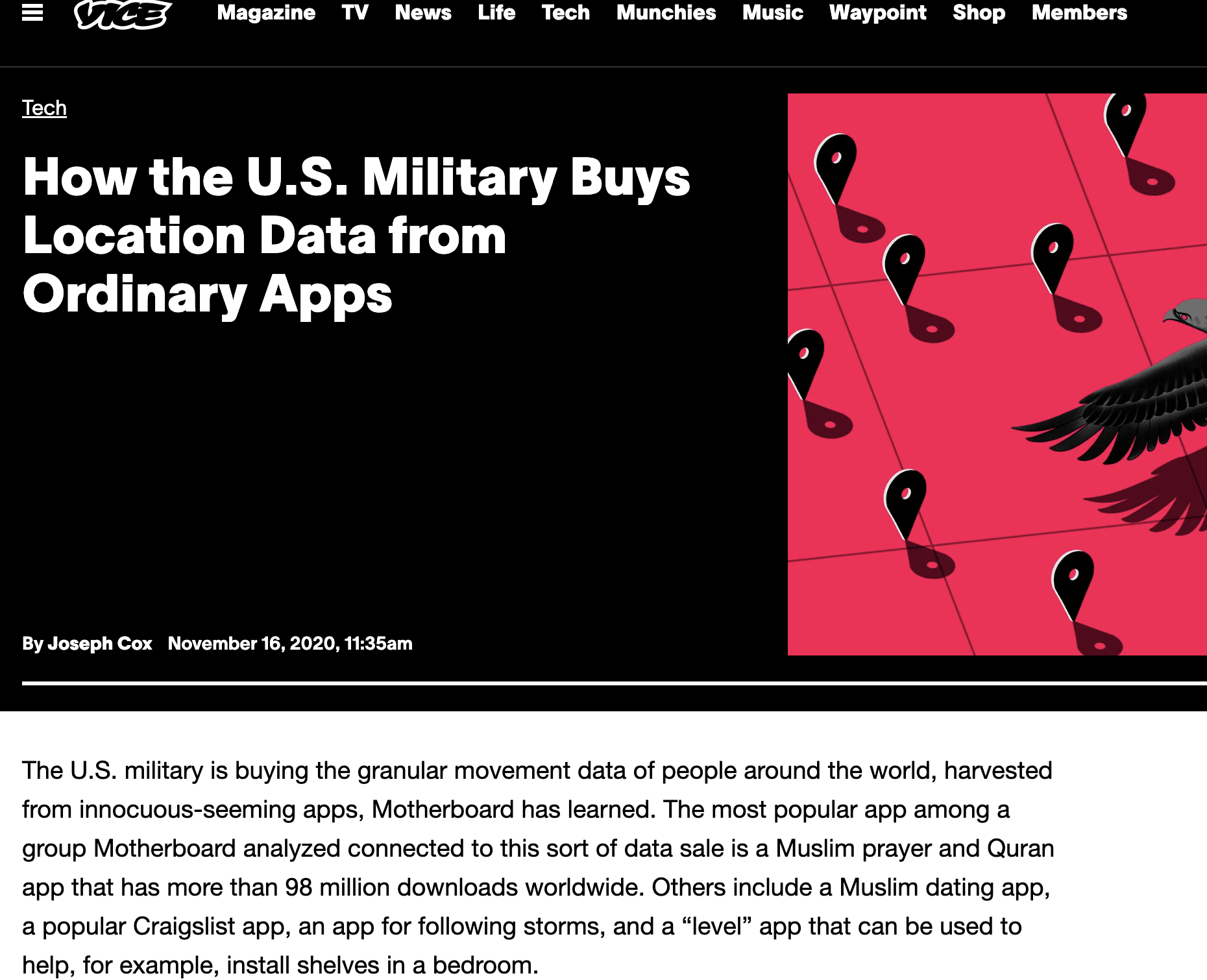
via VICE Motherboard
- 87M Facebook users profiled
- Used to sway voters in US & UK
- Based on “fun” quizzes and likes
Case Study: Political Influence and disinformation
Consequences
- Identity theft & fraud
- Stalking & doxxing
- Manipulation of belief & behavior
- Loss of autonomy
III. What you can flippin do
"The biggest boycott in world history" - Doc Searls, journalist
A. Limit Data at the Source
- Stop using products with bad privacy reputations
- Use privacy-first browsers like Firefox or Brave
- Other helpful browser extensions
- Change your browser's default search engines to DuckDuckGo or Startpage
- Deny unnecessary app permissions (especially location, contacts, photos, camera, microphone)
- Use ad and tracker blocking software
B. Opt Out
- Opt out of pre-screened credit offers
- DMAchoice – direct mail opt-out
- Opt out from data brokers: My Privacy Audit Spreadsheet
- If you're inclined to, there are services that will manage this for you for a fee: DeleteMe, Jumbo, or Privacy Bee to automate this process.
C. Lock Down Social Media
- Set profiles to private
- Limit third-party apps and integrations
- Turn off ad personalization in account settings
- Avoid SSO (“Log in with Google", Facebook, etc)
D. Minimize Digital Footprint
- Use separate “burner” email accounts for signups when possible
- Avoid posting sensitive info (e.g., birth date, location)
- Use pseudonyms where possible
E. Secure Your Devices
- Enable two-factor authentication (2FA)
- Audit your app permissions on your smartphone
- Keep software and OS updated
- Use encrypted messaging apps like Signal
- Encrypt your iCloud data by turning on Advanced Data Protection (iCloud)
F. Make Informed Decisions
- Review privacy policies. Check ToSDR or Privacy Not Included to understand Privacy Policy of services/products
- Follow orgs like EFF, Privacy Rights Clearinghouse, Consumer Reports Innovation
- Use services like Have I Been Pwned to monitor data breaches
Eloquent Conclusion
“If we don’t act to protect privacy, we risk living in a world where our lives are governed not by laws, but by corporate terms of service.” — Shoshana Zuboff, author of The Age of Surveillance Capitalism
"Data rights are human rights" — Carole Cadwalladr
"Politics is technology now" — Carole Cadwalladr